2008-02-10
The main goal of this site is to provide clear, accurate and easy to understand information regarding
You might want to read a short page About this Site and its history.
I do appreciate any support to help defray the monthly costs
If you are mentioning this site in a publication, or found it through one, I would appreciate hearing about it.
Computers are fun, but what I really like to do is .....
For those of you that might want to copy the contents of this site:
It has taken me years to accumulate all this information.
Please take the time to create your own, or...
If you feel this information is valuable, simply link back to the source. This way people get the regular updates
This site is best viewed with at least 1024x768 resolution and 16-bit color
2008-02-03
Artificial Intelligence
· ประกาศคะแนนสอบกลางภาค 2110477 (AI-II)
· ประกาศคะแนนสอบกลางภาค 2110654 (AI)
· 2110477 (AI 2) Final Examination:
Place: Eng. 4, 19-01, Time: 9.00-12.00 (28 September, 2007) !!!
scope—from slide no.1 to slide no.4
· 2110654 (AI) Final Examination:
Place: Eng. 4, 19-01, Time: 9.00-12.00 (27 September, 2007) !!!
scope—from slide no.1 to slide no.4
The slides used in the course:
1st-3rd weeks
slide no.1: Introduction, Problem-Problem Space-Search slide no 1
slide no.2: Tabu Search slide no 2
4th week
slide no.3: Predicate Calculus slide no 3
5th week
slide no.4: Introduction to Prolog slide no 4 (SWI-Prolog's Web Site)
6th-7th weeks
slide no.5: Natural Language Processing slide no 5
8th weeks
Midterm Examination (scope—from slide no.1 to slide no.4)
9th week
slide no.6: Genetic Algorithm slide no 6
10th week
slide no.7: Rote Learning, Learning by Analyzing Differences, Version Spaces slide no 7 (A Prolog Implementation of Version Space)
11th week
slide no.8: Decision-Tree Learning, Explanation-Based Learning slide no 8(A Decision-Tree Software: See 5’s Web Site, download CUMiner and .NET Framework) (A Prolog Implementation of EBL)
12th week
slide no.9: Inductive Logic Programming slide no 9
13th week
slide no.10: Artificial Neural Networks slide no 10 (NeuroSolutions’ Web Site)
14th week
slide no.11: Bayesian Learning slide no 11
15th week
Other topics : slide no.12: Support Vector Machines slide no 12
16th week
Final examination (scope—from slide no.6 to slide no.12)
The lecture notes:
Lecture note no.1: Introduction to Artificial Intelligence lecture note no 1
Lecture note no.2: Problem, Problem Space and Search lecture note no 2
Lecture note no.3: Predicate Logic lecture note no 3
Lecture note no.4: Prolog lecture note no 4
Lecture note no.5: Genetic Algorithm lecture note no 5
Lecture note no.6: Rote Learning lecture note no 6
Lecture note no.7: Learning by Analyzing Differences lecture note no 7
Lecture note no.8: Version Space lecture note no 8
Lecture note no.9: Decision Tree Learning lecture note no 9
Lecture note no.10: Explanation-Based Learning lecture note no 10
Lecture note no.11: Neural Networks lecture note no 11
Lecture note no.12: Bayesian Learning lecture note no 12
If you have comments, suggestions, etc., give them to me at http://www.cp.eng.chula.ac.th/course/forum/?cat=2110477
Assignment1: data.dat
References:
E.Rich & K.Knight, Artificial Intelligence, Second Edition, McGraw-Hill
S. Russell & P.Norvig, Artificial Intelligence: A Modern Approach, Second Edition, Prentice Hall.
MIT Computer Science and Artificial Intelligence Laboratory
Tuesday February 5th:Robotics Seminar Series Spring 2008: From Biologically Inspired Robots to Reality: Snake and Quadruped Walking
Wednesday February 6th: Robotics Seminar Series Spring 2008: Real-Time Adaptive Signal Processing

2008-02-01
OstroSoft Internet Tools
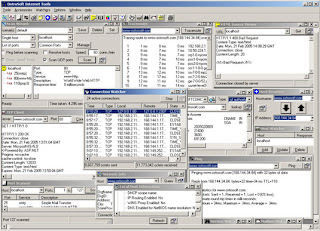 It gives you such vital information as:
It gives you such vital information as:which computers on domain are running specified service - for example: how many newsservers are available on domain (Domain Scanner)
what network services are running on specified computer (remote or local) - for example: Web server, telnet, mailserver, FTP, finger, etc. (Port Scanner)
let you test if remote host is running, accessible from your system, and how long it takes to reach it (Ping)
shows you the path TCP packet takes from your system to remote host (Traceroute)
shows you the information about active connections on you computer (Netstat)
resolves host names to IP addresses and vice versa (Host Resolver - dns)
returns contact information (address, phone, fax, administrator name, DNS servers) for specified network (Network Info)
shows network-related information (IP address, host name, version of Winsock, etc.) about your computer (Local Host Info) It helps to find hidden resources on network. It reveals security holes and helps to fix it. It is fast, reliable and user-friendly. And it is getting better with every release. OstroSoft Internet Tools is not intended for hacking purposes, malicious attacks on networks and systems connected to the network, and other unlawful actions.
MP3 Normalizer
Minimum requirements: VB4
Download: source code
Screenshot:

Controls: fm (Frame), cmdDown (CommandButton), cmdUp (CommandButton), cmdFix (CommandButton), cmdApply (CommandButton), txtTitle (TextBox), txtArtist (TextBox), txtFile (TextBox), lbl (Label), lbl (Label), lbl (Label), File1 (FileListBox), Dir1 (DirListBox), Drive1 (DriveListBox)
Code:
Option Explicit
Dim sDir As String
Private Sub cmdApply_Click()
If Len(txtArtist) > 30 Then
If MsgBox("Artist tag is longer than 30 characters" & vbCrLf & _
" Would you like to truncate it?", vbYesNo, "Warning") = vbYes Then
txtArtist = Trim(Left(txtArtist, 27)) & "..."
Else
MsgBox "Unable to apply changes", , "Error"
End If
Exit Sub
End If
If Len(txtTitle) > 30 Then
If MsgBox("Title tag is longer than 30 characters" & vbCrLf & _
" Would you like to truncate it?", vbYesNo, "Warning") = vbYes Then
txtTitle = Trim(Left(txtTitle, 27)) & "..."
Else
MsgBox "Unable to apply changes", , "Error"
End If
Exit Sub
End If
If Len(txtFile) > 255 Then
If MsgBox("File name is longer than 255 characters" & vbCrLf & _
" Would you like to truncate it?", vbYesNo, "Warning") = vbYes Then
txtFile = Trim(Left(txtFile, 255))
Else
MsgBox "Unable to apply changes", , "Error"
End If
Exit Sub
End If
If InStr(txtFile, "*") > 0 Or InStr(txtFile, "?") > 0 Then
MsgBox "Special characters from file name will be removed", , "Warning"
txtFile = Replace(txtFile, "*", "")
txtFile = Replace(txtFile, "?", "")
Exit Sub
End If
Me.MousePointer = vbHourglass
If Dir(File1.Path & "\new", vbDirectory) = "" Then MkDir File1.Path & "\new"
Name File1.Path & "\" & File1.List(File1.ListIndex) As File1.Path & "\new\" & txtFile
SetTag File1.Path & "\new\" & txtFile, txtTitle, txtArtist
File1.Refresh
txtFile = "": txtTitle = "": txtArtist = ""
If File1.ListCount > 0 Then File1.ListIndex = 0
Me.MousePointer = vbDefault
End Sub
Private Sub cmdDown_Click()
If InStr(txtFile, "-") <> 0 Then
txtArtist = Left(txtFile, InStr(txtFile, "-") - 1)
txtArtist = Replace(txtArtist, "_", " ")
txtArtist = Capitalize(txtArtist)
End If
txtTitle = Mid(txtFile, InStr(txtFile, "-") + 1)
txtTitle = Left(txtTitle, Len(txtTitle) - 4)
txtTitle = Replace(txtTitle, "_", " ")
txtTitle = Capitalize(txtTitle)
End Sub
Private Sub cmdFix_Click()
txtFile = Replace(txtFile, " ", "_")
txtFile = Replace(txtFile, "_-_", "-")
txtFile = Replace(txtFile, "(", "")
txtFile = Replace(txtFile, ")", "")
End Sub
Private Sub cmdUp_Click()
txtFile = txtArtist & "-" & txtTitle & ".mp3"
txtFile = Replace(txtFile, " ", "_")
End Sub
Private Sub Dir1_Change()
File1.Path = Dir1.Path
If File1.ListCount > 0 Then File1.ListIndex = 0
End Sub
Private Sub Drive1_Change()
Dim sDrive As String
sDrive = Drive1.Drive
If InStr(sDrive, "[") <> 0 Then sDrive = Trim(Left(sDrive, InStr(sDrive, "[") - 1))
sDrive = sDrive & "\"
Dir1.Path = sDrive
End Sub
Private Sub Form_Load()
sDir = GetSetting("mp3_norm", "StartUp", "Dir", "")
If Dir(sDir, vbDirectory) <> "" And Dir(sDir, vbDirectory) <> "." Then
Drive1.Drive = Left(sDir, InStr(sDir, ":") - 1)
Dir1.Path = sDir
End If
End Sub
Private Sub File1_Click()
Dim sFile As String
sFile = File1.Path & "\" & File1.List(File1.ListIndex)
Dim sArtist As String
Dim sTitle As String
txtFile = File1.List(File1.ListIndex)
txtTitle = ""
txtArtist = ""
If GetTag(sFile, sTitle, sArtist) Then
txtTitle = Capitalize(sTitle)
txtArtist = Capitalize(sArtist)
End If
End Sub
Private Function GetTag(ByVal sFile As String, sTitle As String, sArtist As String) As Boolean
Dim b As Byte
Dim l As Long
Dim s As String
l = FileLen(sFile) - 1
Open sFile For Binary Access Read As 1
While FileLen(sFile) - l < 128
l = l - 1
Get #1, l, b
s = Chr(b) & s
Wend
Close #1
If InStr(s, "TAG") <> 0 Then
s = Mid(s, InStr(s, "TAG") + 3)
For l = 1 To 30
sTitle = sTitle & RusLat(Mid(s, l, 1))
Next
For l = 31 To 60
sArtist = sArtist & RusLat(Mid(s, l, 1))
Next
sTitle = Trim(sTitle)
sArtist = Trim(sArtist)
GetTag = True
Else
GetTag = False
End If
End Function
Private Function SetTag(ByVal sFile As String, sTitle As String, sArtist As String) As Boolean
Dim b As Byte
Dim l As Long
Dim lPos As Long
Dim s As String
Dim i As Integer
l = FileLen(sFile)
Open sFile For Binary Access Read Write As 1
While FileLen(sFile) - l < 128
Get #1, l, b
s = Chr(b) & s
l = l - 1
Wend
If InStr(s, "TAG") <> 0 Then
s = Left(s, InStr(s, "TAG") - 1)
l = FileLen(sFile) - 127 + Len(s)
Else
s = ""
l = FileLen(sFile) - 1
End If
s = s & "TAG" & txtTitle & Space(30 - Len(txtTitle)) & txtArtist & Space(30 - Len(txtArtist)) & Space(64)
For lPos = l To l + Len(s) - 1
i = i + 1
Put #1, lPos, Asc(Mid(s, i, 1))
Next
Close #1
End Function
Private Function Capitalize(ByVal s As String) As String
Dim i As Integer
s = UCase(Mid(s, 1, 1)) & LCase(Mid(s, 2))
For i = 2 To Len(s)
If Mid(s, i, 1) = " " Or Mid(s, i, 1) = "." Or Mid(s, i, 1) = "," Then
If i <> Len(s) Then s = Left(s, i) & UCase(Mid(s, i + 1, 1)) & Mid(s, i + 2)
End If
Next
Capitalize = s
End Function
Private Function RusLat(ByVal s As String) As String
Select Case Asc(s)
'lower case
Case &HB8: RusLat = "yo"
Case &HE9: RusLat = "y"
Case &HF6: RusLat = "ts"
Case &HF3: RusLat = "u"
Case &HEA: RusLat = "k"
Case &HE5: RusLat = "e"
Case &HED: RusLat = "n"
Case &HE3: RusLat = "g"
Case &HF8: RusLat = "sh"
Case &HF9: RusLat = "sch"
Case &HE7: RusLat = "z"
Case &HF5: RusLat = "kh"
Case &HFA: RusLat = "y"
Case &HF4: RusLat = "f"
Case &HFB: RusLat = "i"
Case &HE2: RusLat = "v"
Case &HE0: RusLat = "a"
Case &HEF: RusLat = "p"
Case &HF0: RusLat = "r"
Case &HEE: RusLat = "o"
Case &HEB: RusLat = "l"
Case &HE4: RusLat = "d"
Case &HE6: RusLat = "zh"
Case &HFD: RusLat = "e"
Case &HFF: RusLat = "ya"
Case &HF7: RusLat = "ch"
Case &HF1: RusLat = "s"
Case &HEC: RusLat = "m"
Case &HE8: RusLat = "i"
Case &HF2: RusLat = "t"
Case &HFC: RusLat = "'"
Case &HE1: RusLat = "b"
Case &HFE: RusLat = "yu"
'upper case
Case &H98: RusLat = "Yo"
Case &HE9: RusLat = "Y"
Case &HD6: RusLat = "Ts"
Case &HD3: RusLat = "U"
Case &HCA: RusLat = "K"
Case &HC5: RusLat = "E"
Case &HCD: RusLat = "N"
Case &HC3: RusLat = "G"
Case &HD8: RusLat = "Sh"
Case &HD9: RusLat = "Sch"
Case &HC7: RusLat = "Z"
Case &HD5: RusLat = "Kh"
Case &HDA: RusLat = "Y"
Case &HD4: RusLat = "F"
Case &HDB: RusLat = "I"
Case &HC2: RusLat = "V"
Case &HC0: RusLat = "A"
Case &HCF: RusLat = "P"
Case &HD0: RusLat = "R"
Case &HCE: RusLat = "O"
Case &HCB: RusLat = "L"
Case &HC4: RusLat = "D"
Case &HC6: RusLat = "Zh"
Case &HDD: RusLat = "E"
Case &HDF: RusLat = "Ya"
Case &HD7: RusLat = "Ch"
Case &HD1: RusLat = "S"
Case &HCC: RusLat = "M"
Case &HC8: RusLat = "I"
Case &HD2: RusLat = "T"
Case &HDC: RusLat = "'"
Case &HC1: RusLat = "B"
Case &HDE: RusLat = "Yu"
Case Else: RusLat = s
End Select
End Function
Private Sub Form_Unload(Cancel As Integer)
SaveSetting "mp3_norm", "StartUp", "Dir", File1.Path
End Sub
2008-01-31
Creating Snapshot-Backups with FlyBack On Ubuntu 7.10
I do not issue any guarantee that this will work for you!
1 Installing FlyBack
In order to install FlyBack, we open a terminal (Applications > Accessories > Terminal):
 First we install FlyBack's dependencies as follows:
First we install FlyBack's dependencies as follows:sudo apt-get install python python-glade2 python-gnome2 python-sqlite python-gconf rsync
 Then we download and unpack FlyBack (in our home directory) like this:
Then we download and unpack FlyBack (in our home directory) like this:cd ~wget http://flyback.googlecode.com/files/flyback_0.4.0.tar.gztar -zxvf flyback_0.4.0.tar.gz
That's it already, FlyBack can now be used.
2 Using FlyBack
It's a good idea to store your backups on an external hard drive. Please plug in an external hard drive and wait until it gets mounted (an icon should then appear on your desktop):
cd ~/flyback/python flyback.py
FlyBack starts. If you see the following error message, simply click on OK - you can ignore this error:

FlyBack starts with the Preferences window. On the Storage Location tab, select your external hard drive:


 ... and click on the Add button:
... and click on the Add button:
 The selected directory should now be listed under included dirs. Repeat this step for as many directories as you want to back up. The exclude patterns field already contains a good default selection of files/directories not to back up. Modify it only if you know what you're doing:
The selected directory should now be listed under included dirs. Repeat this step for as many directories as you want to back up. The exclude patterns field already contains a good default selection of files/directories not to back up. Modify it only if you know what you're doing:

On the Backup Schedule tab you can automate FlyBack backups if you like:

Please note that FlyBack doesn't have to be running if you've selected to create automatic backups on the Backup Schedule tab. FlyBack creates a cron job for it. You can check that by opening a terminal and running:
crontab -l
In the output there should be a cron job for FlyBack (e.g. like this, running at the selected time):
falko@falko-desktop:~$ crontab -l0 3 * * * python /home/falko/flyback/flyback.py --backup #flybackfalko@falko-desktop:~$
Now that we've configured FlyBack to our likings, we can close the Preferences window.
The main window looks as follows, showing you the contents of your hard drive. The right window (system snapshots) lists all available backups - as we've created none yet, it only shows now which refers to the actual content of your hard drive.
 You can browse the contents of your hard drive like you know it from your default file browser. The Home button takes you to your home directory (e.g. /home/falko):
You can browse the contents of your hard drive like you know it from your default file browser. The Home button takes you to your home directory (e.g. /home/falko):
VB projects - Centering the form caption
Minimum requirements: vb
Download: source code
Screenshot:

Project: Standard EXE
Controls: Label1 (label)
Code:
Dim i As Integer 'size of space
Dim iCap As Integer 'size of caption
Private Const txt = "This is the test" 'form caption text
Private Sub Form_Load()
With Label1
.AutoSize = True
.FontName = "MS Sans Serif"
.FontBold = True
.FontSize = 8
.Caption = " "
i = .Width - 15
.Caption = txt
iCap = .Width - 15
.Visible = False
End With
End Sub
Private Sub Form_Resize()
If WindowState <> vbMinimized Then
If Width < iCap + 1300 Then Width = (iCap + 1300)
Caption = String((Width - (iCap + 1300)) / (2 * i), " ") & txt
End If
End Sub
Animation, using picture control
Minimum requirements: VB6
Download: source code
Screenshot:

Project: EXE
Controls: cmdDirection (Command Button, Caption = "go back"), tmr (Timer, Interval = 20), pic (PictureBox, AutoSize = -1 'True, BorderStyle = 0 'None)
Additional references: none
Code:
Option Explicit
Dim i As Integer
Dim j As Integer
--------------------------------------------------------------------------------
Private Sub cmdDirection_Click()
If cmdDirection.Caption = "go back" Then
cmdDirection.Caption = "go"
j = -60
Else
cmdDirection.Caption = "go back"
j = 60
End If
End Sub
--------------------------------------------------------------------------------
Private Sub Form_Load()
Set pic.Picture = LoadPicture("untitled1.bmp")
i = 1
j = 60
End Sub
--------------------------------------------------------------------------------
Private Sub tmr_Timer()
If i < 8 Then i = i + 1 Else i = 1
If (pic.Left < Me.Width And j > 0) Or (pic.Left > 0 And j < 0) Then
pic.Left = pic.Left + j
Set pic.Picture = LoadPicture("untitled" & i & ".bmp")
End If
End Sub
Adjust flexgrid cell width
Minimum requirements: VB6
Download: source code
Screenshot:

Project: EXE
Controls: CommandButton cmdEnter, TextBox txt, MSFlexGrid grd, Label lbl (AutoSize = -1 'True)
Additional references: none
Code:
Option Explicit
--------------------------------------------------------------------------------
Private Sub cmdEnter_Click()
grd.Text = txt
lbl.FontName = grd.CellFontName
lbl.FontSize = grd.CellFontSize
lbl = grd.Text
grd.ColWidth(grd.Col) = lbl.Width + 120
End Sub
ipconfig
Minimum requirements: VB4
Download: source code
Screenshot:

Controls: cmd (CommandButton), txt (TextBox)
Code:
Option Explicit
Private Const OS_ERROR = -1
Private Const OS_95 = 1
Private Type OSVERSIONINFO
dwOSVersionInfoSize As Long
dwMajorVersion As Long
dwMinorVersion As Long
dwBuildNumber As Long
dwPlatformId As Long
szCSDVersion As String * 128
End Type
Private Declare Function GetVersionEx Lib "kernel32" Alias "GetVersionExA" _
(LpVersionInformation As OSVERSIONINFO) As Long
Private Declare Function OpenProcess Lib "kernel32" (ByVal dwDesiredAccess As Long, _
ByVal bInheritHandle As Long, ByVal dwProcessId As Long) As Long
Private Declare Function GetExitCodeProcess Lib "kernel32" _
(ByVal hProcess As Long, lpExitCode As Long) As Long
Private Declare Function CloseHandle Lib "kernel32" (ByVal hObject As Long) As Long
Private Const PROCESS_QUERY_INFORMATION = &H400
Private Sub cmd_Click()
Dim nOS As Long
Dim temp As String, bDNS As Boolean
Dim hProcess As Long
Dim ProcessId As Long
Dim exitCode As Long
Me.MousePointer = vbHourglass
nOS = GetOSVersion
If nOS = OS_ERROR Then
MsgBox "Unsupported operating system"
Exit Sub
End If
txt = ""
Open App.Path & "\ip.bat" For Output As 1
If nOS = OS_95 Then
Print #1, "Winipcfg.exe /all /batch " & App.Path & "\1.txt"
Print #1, "ren " & App.Path & "\1.txt ip.txt"
Else
Print #1, "ipconfig /all > " & App.Path & "\ip.txt"
End If
Close #1
While Dir(App.Path & "\ip.bat") = ""
DoEvents
Wend
ProcessId = Shell(App.Path & "\ip.bat", vbHide)
If nOS = OS_95 Then
While Dir(App.Path & "\ip.txt") = ""
DoEvents
Wend
Else
hProcess = OpenProcess(PROCESS_QUERY_INFORMATION, False, ProcessId)
Do
Call GetExitCodeProcess(hProcess, exitCode)
DoEvents
Loop While exitCode > 0
End If
CloseHandle hProcess
Open App.Path & "\ip.txt" For Input As 1
While Not EOF(1)
Line Input #1, temp
If Trim(temp) <> "" Then txt = txt & Trim(temp) & vbCrLf
Wend
Close #1
Kill App.Path & "\ip.bat"
Kill App.Path & "\ip.txt"
Me.MousePointer = vbNormal
End Sub
Private Sub Form_Load()
cmd_Click
End Sub
Private Function GetOSVersion() As Long
Dim os As OSVERSIONINFO
Dim nRet As Long
os.dwOSVersionInfoSize = Len(os)
nRet = GetVersionEx(os)
If nRet = 0 Then
GetOSVersion = -1
ElseIf os.dwPlatformId = 0 Then '"Windows 32s "
GetOSVersion = -1 'not supported by this program
Else
GetOSVersion = os.dwPlatformId
End If
End Function
Network coding: Networking's next revolution?
Network coding, largely shrouded in university and vendor labs since it was proposed seven years ago by a handful of researchers, is essentially an algorithm that proponents say can potentially more than double network throughput while also improving reliability and resistance to attacks. According to network coding's most ardent supporters, the technology could spark networking's next revolution, while others said network coding is more likely to quietly infiltrate network architectures based on existing routing schemes.
Network coding works by separating messages into smaller bits of "evidence" that can then be deduced by the destination node without transmitting, retransmitting or replicating the entire message. It enables this evidence to traverse multiple paths to and from intermediary nodes that then send it on to the endstation. It does not require additional capacity or routes -- it simply mixes evidence of messages into bit streams already supported by an existing network infrastructure.
"It's like eavesdropping. You listen to what's going on around you, you form an opinion and then you improve the overall throughput and capacity by actually remembering and using the information you have," said Sumeet Sandhu, principal investigator for cooperative wireless communication at Intel Research.
Network coding could work its way into any number of products from routers to wireless systems or take the form of entirely new devices dubbed network coders. Intel sees the potential for the technology to extend the range of wireless base stations. Microsoft is already trialing network coding to make its content distribution system more efficient (read "Microsoft's network coding plan").
Other big network players, such as Cisco Systems Inc., are keeping their plans hush hush for now and declined to say more than this, through a spokesman: "We are investigating network coding as the theory helps distinguish a variety of different types of traffic, then prioritizes them to help increase the capacity of the network. Right now, we do not offer any specific network coding products."
Decoding network coding
To give you a better feel for what network coding is all about, here's a further technical explanation.
Network coding manipulates the data inside the packet itself through what's called a "bitwise exclusive or" (xor) operation to combine the information with that of another packet. A bitwise xor takes two bit patterns and performs the logical operation on each pair of corresponding bits, assigning a number "1" if the two bits are different and "0" if they are the same.
These 1s and 0s are the codes, or evidence, by which an endstation or any node with the intelligence to do so can deduce the message received from the sender. In this manner, network coding effectively allows destination nodes to receive multiple messages without an increase in the number of packets it receives or in overall network capacity.
"You're using the algebraic nature of the data in order to give yourself more freedom with what you can do with the packets," said Muriel Medard, an associate professor in the electrical engineering and computer science department at MIT, and a leading researcher in the field of network coding. "You can do things within the network that allow you to use it more efficiently or in different ways."
Proponents like Medard said network coding is particularly beneficial in shared router infrastructures -- such as the Internet -- peer-to-peer content distribution and wireless mesh networks. In an article describing the concept, Medard and other researchers stated that network coding has the potential to dramatically speed up and improve the reliability of all manner of communications systems and may well spark the next revolution in the field.
How a network operator implements network coding depends on what the operator is looking to accomplish, Medard said. It differs from Multiprotocol Label Switching traffic engineering -- another, widely implemented method for increasing network capacity and efficiency -- in that MPLS does not change the data within a packet; it adds an appendage, or label, to the packet ("MPLS explained").
"You're not just working on whatever fields of a packet you've selected to work on.
You're actually considering the possibility of working and operating on the data itself inside the packet," Medard said. "But in the end, you still recover the information you originally wanted."
Current router and switching systems do not do this. They read the source and destination fields of packets and direct traffic accordingly by mapping input to outputs on the same node -- they do not combine the contents of two different packets, nor do they map inputs on one node to outputs on another.
"But the ability to do something like xor can really benefit you quite a bit in the operation of your network," Medard said. "By giving yourself the freedom of doing that ... you're dramatically changing the landscape of what you can do."
Medard said network coders may not replace routers per se, but could function as an overlay to routing. But over time, network coding could become integral to the routing operation as its benefits become evident, essentially changing routing technology as we know it today.
Medard said she presented her technical research to Cisco engineers two or three years ago. She characterized the talk as "good" but stressed that it was technical and no commercial implications were discussed.
HP's take on network coding
HP, like Microsoft, sees network coding having promise for peer-to-peer content distribution. HP is also collaborating with and funding MIT's work in the field.
"It's an exciting new technique," said Mitchell Trott, a researcher at HP Labs. "It has a lot of potential, but it's not clear exactly which systems are going to benefit from it."
An application for network coding in the network infrastructure is "a tougher question" than whether network coding can aid in content distribution, Trott said. It must be proved that it provides a large performance gain before infrastructure vendors adopt it, he said.
"You have to have a particular problem to solve -- multicast is probably the one that would most benefit," he said. "But, of course, most people don't even have multicast turned on."
Multicast, which delivers information to a group of destinations simultaneously, can be made more efficient by network coding in the same manner that traditional routing can be improved.
Multicast creates copies of entire messages when the links to the destinations split, but network coding can alleviate that through its xor evidence technique, researchers said.
Another factor making network coding questionable for network infrastructure, Trott said, is that switches and routers tend to sit in equipment racks for up to a decade.
"It would take quite a while to roll over the equipment to support these new techniques," Trott said. There would also have to be new control and management protocols developed to track all of the packet and bit stream manipulations that coding routers and switches -- or coders -- perform in the network, and how their neighbor nodes are notified, he said.
"It's one of these things which is I think a little bit hard to roll out gradually," Trott said. "You can roll out the capability gradually, but you have to turn it on all at once."
So far, HP hasn't quite found a fit for network coding in commercial products, but Trott said that could change over time. He also said wireless mesh networks could benefit from the technique, especially ad hoc military sensor networks.
MIT researchers conducted research that shows coding provides a "severalfold increase" in throughput of wireless networks. MIT researchers said they saw a doubling of throughput in a very small setting and as much as fourfold in an experiment using User Datagram Protocol traffic involving 34 nodes on three floors of an MIT building.
Intel's into network coding
Intel also expects network coding to benefit its wireless initiatives, specifically in WiMax. Intel began its network coding research in 2006.
Multihop relay -- in which WiMax base stations and relay stations are controlled by the infrastructure -- can benefit from network coding in extending the range of a base station, said Intel Research's Sandhu. The relay stations perform wireless backhaul to the base station, and network coding can make two-way relay in the middle of an end-to-end base station-to-client interaction more efficient by minimizing redundant packet routing, she said. In this application, network coding can provide throughput gains of 25% to 50% in simple two-way routing, she added.
"You save time by doing this xor in the middle," Sandhu said. "Instead of four time slots to do the end-to-end two-way communication, it only takes you three slots because in one slot you actually combine the two packets and send them out."
But WiMax is not an ad hoc network like a military sensor network would be -- it's centralized.
A base station serving a cell with perhaps a few relays thrown in for range extension is usually the norm for a WiMax network, Sandhu noted.
"It's not a very rich infrastructure; there's limited scope to play games with new tricks like network coding," she said. "So we're looking at this very simple two-way network only so far."
Intel's looking at network coding's applicability at the physical layer of the OSI reference model as well for how it interacts with antennas in a multiple-input, multiple-output environment, Sandhu said. Physical layer information may be lost as bits move up to the Media Access Control layer, so Intel is looking at ways to capture the physical layer channel information to do more optimal network coding.
Sandhu could not say whether Intel has any product development planned or under way around network coding. But Sandhu said she does see its applicability to data communications across the board in addition to wireless and WiMax.
What about security?
This concept of eavesdropping and xor bitstream intermingling does raise security concerns, researchers acknowledged.
But MIT's Medard said network coding -- with its ability to essentially disguise message and payload data -- can actually enhance information security beyond encryption and cryptography by making traffic traversing networks an undecipherable algebraic stream.
"When you do this combination it has a data-hiding aspect," Medard said. "When you have two bits, A and B, and you xor the two, seeing the xor you don't know what either bit was. You may know something about the pair of the bits, but you can't figure out bit A unless you know bit B perfectly."
Network coding techniques also provide the ability to detect malicious "pollution" attacks in peer-to-peer interactions and correct them, she said.
Still, much research needs to be done to determine network coding's impact on security and a number of other issues beyond whether network coders will eventually supplant routers in large, shared infrastructures like the Internet. Users have to know how and when to implement network coding in cases where information cannot be mixed on a shared network; they must also consider the nuances between network coding in wired and wireless infrastructures; and the industry must determine how customers will be charged for telecommunications services when carriers mix customer traffic together.
Medard said she and others are considering such issues as they continue to delve into methods to improve the networks that are increasingly becoming more integral to society.
VoIP on 3G will beat Wi-Fi
Mobile VoIP is set to grow, but it will run over the 3G data provided by cellular handsets, rather than over Wi-Fi, according to a research report from Disruptive Analysis Ltd., which predicts 250 million users of 3G VoIP by 2012, compared with less than 100 million for voice on Wi-Fi.
"Yes, 250 million is a surprisingly big number," said Dean Bubley of Disruptive Analysis. "I did the sums and then had to triple-check my own model. The fundamental truth, he said, is that mobile networks are moving toward Long Term Evolution or possibly Ultra Mobile Broadband technology and that will be all IP based, so for operators "VoIP is mandatory."
VoIP will allow carriers to handle more calls on their scarce spectrum and backhaul, and reduce expenses by handling all traffic as data. It will also let them offer new services such as push-to-talk and voice-integrated "mashups," said Bubley, in his report, VoIPo3G Business Models.
VoIP on 3G also fits the move to femtocells, which use the subscribers' broadband service to increase coverage in the home, since the digitized voice is ready to be handled by the femto's broadband backhaul.
However, because new radio technologies are not yet widespread, we can look forward to a few more years of the current confusion while third-party providers such as Truphone and EQO Communications Inc. (and many others) offer mobile VoIP using Wi-Fi services or the user's data plan. "Some independent VoIP players are already exploiting the fact that today's 3G networks can already support VoIP, putting dedicated software on smart phones, exploiting open operating systems, flat-rate data plans and features like 'naked SIP' and built-in VoIP capability," said Bubley.
The rise of mobile data in laptops, either as built-in modems or data cards will also contribute to the growth of VoIP on 3G, as this service often competes with home broadband, and users expect to be able to use familiar applications such as Skype or other telephony software. "Some operators are even offering their own VoIP software for PCs with wireless broadband," said Bubley.
"By 2012, most VoIPo3G users will be using mobile carriers' own standards-based VoIP capabilities, over the new, advanced 3G+ networks," said Bubley. Only 60 million of them will still be on the independent operators' offerings. "The key thing to think about is that for many users, VoIP will be invisible."
And there will still be more to go, because 250 million will only be about 10% of mobile phone users, and 20% of 3G+ users.
The most wired school in America
 The technology in corporate America is thriving, creating a Future World environment that provides instant access to anything imaginable. But what about America's schools? Without the expertise and financial resources of a profit-based corporation, how can the educational community keep pace with the future job requirements of the global markets?
The technology in corporate America is thriving, creating a Future World environment that provides instant access to anything imaginable. But what about America's schools? Without the expertise and financial resources of a profit-based corporation, how can the educational community keep pace with the future job requirements of the global markets?"There is no 'silver bullet' answer to the problems in education," says Mary Cullinane, director of Microsoft U.S. Partners in Learning. "But one important conclusion is that education institutions face many problems when designing and building quality learning environments for their students. We, as a company and a member of their community, need to figure out a better way to support them. At the end of the day, it's about the kids, and being able to help address the challenges our country is facing is truly a privilege."
Better ways
Enter the School of the Future (SOF) and see that "better way" in action. Located on seven acres in West Philadelphia's Fairmount Park, this new, very futuristic facility is at the top of the list for the most wired school in America. However, in this case, the most wired school in America is, in fact, mostly wireless.
The School of the Future opened its doors in September 2006. Funded by the School District of Philadelphia with additional support and technical assistance from Microsoft Corp., this $63 million project is a technological inspiration for other educational institutions across the globe.
All the students and educators carry Gateway laptops with fiber-optic Internet connectivity.
"The school can handle 750 students, four grades," says Barbara Farley, director of the office of communications at the school district of Philadelphia. "Currently, we have grades 9 and 10 enrolled in the SOF, approximately 400 students. In two years, the entire student body will be included in the SOF's curriculum and technology. However, we want it to be known that it's not just about the technology."
"Our philosophy," says Robin Walker, development coordinator at the SOF, "is to be sure that the curriculum drives the technology and not the other way around. We place the emphasis on learning first, with technology second."
"In addition," says Rosalind Chivis, SOF associate superintendent for curriculum and instruction, "we wanted to build a replicable school using processes (both educational and technological) that work as an incubator for best practices, to make this project scalable districtwide."

All the students and educators carry Gateway laptops with fiber-optic Internet connectivity provided by the Meru Wireless LAN System, and each user has his own personalized media portal. "Wireless access is available throughout the facility, including the physical education center and the amphitheater outside the building," says Bob Westall, deputy CIO at the SOF.
All the classrooms have wireless Panasonic projectors, wireless microphones and Promethean whiteboards, which allow interactive activities and assignments between students and teachers, adds Westall. They also have access to a variety of digital devices such as digital cameras, camcorders and webcams for their project-based learning assignments, which they can use and share online or on one of the seven 42-in. Panasonic plasma screens located throughout the facility. "In addition, there are 30 surveillance cameras throughout the buildings to ensure a safe environment for everyone."
Smart cards are issued to everyone for lockers, building access, the digital library (called the Interactive Learning Center, which offers online textbooks containing local, regional and global information that's always current) and meals in a food court that rivals any mall in America. These cards also track attendance, library usage and food purchased -- plus they provide data on diet, nutrition and caloric intake.
The software used at the SOF includes Microsoft's Exchange Server, Identity Lifecycle Manager, Office SharePoint Server, Vista, Microsoft Office and Microsoft Student with Encarta Premium. In addition, Microsoft developed a Virtual Teaching Assistant program tailored to the school's specific needs, which provides the teachers with active, online tracking to monitor the students' progress and development areas. Teachers can create a test or assignment, send it directly to the students' laptops, then grade it immediately when they complete the exercise.
Design technologies
The architectural design is equally impressive. The 162,000-square-foot, four-story building (three floors above ground with a sort of daylight basement that conforms to the natural grade of the landscape) is Gold LEED-certified for its environmental design and construction. Gold LEED is the benchmark developed by the U.S. Green Building Council that rates buildings based on compliance in six environmental areas, adds Edison Freire, manager of the educational technology group.
The first floor has a "street scape" that resembles a boardwalk with direct access to the adaptive functional modules; that is, classrooms and other self-contained spaces linked by structure. Each module can expand, contract or integrate based on program requirements and/or site characteristics. For example, the auditorium (also known as the Performance Arts Center) located on the lower level is 8,500 square feet, seats 500 and has rotating platforms on a hydraulic system to divide the full auditorium area into smaller spaces (called pods) for events with audiences of 100 or less.
 Photovoltaic panels in the glass windows and roof reduce heating and cooling costs by converting sunlight into direct current, and photoelectric glass, which generates some of the building's power supply, also transmits real-time data for students to study the energy generated and the positive impact this has on the environment.
Photovoltaic panels in the glass windows and roof reduce heating and cooling costs by converting sunlight into direct current, and photoelectric glass, which generates some of the building's power supply, also transmits real-time data for students to study the energy generated and the positive impact this has on the environment.Photovoltaic panels in the glass windows and roof reduce heating and cooling costs by converting sunlight into direct current, and photoelectric glass, which generates some of the building's power supply, also transmits real-time data for students to study the energy generated and the positive impact this has on the environment.
"The 11,000-square-foot auditorium roof is covered with grass and shade trees to shield it from ultraviolet rays, control water runoff during rainstorms and reduce the urban-heat island effect," says Freire. In addition, the roof supports a recycled water system that collects rainwater and gravity feeds it into a 30,000-gallon underground tank, which is pumped back up to the school for flushing toilets and servicing the boiler system. Also, an ice-storage system makes ice during the off hours to help cool the building, notes Freire.
Further recycling efforts include using leftover wood from the construction site to build student desks, and using trees removed from the site prior to construction to build classroom and kitchen cabinets. In addition, the Forest Stewardship Council reported that 40% of all the wood used in this project was harvested according to its policies and approval. Plus, more than 70% of the waste from the construction was recycled, paving the way for the school's comprehensive recycling program that manages the facility's waste paper, metals and plastics.
Teaching and learning technologies
"What's really new in this environment is the way the technology is leveraged," says Chivis. "Instead of teaching the core curriculum as 'subject-based' education, which is the standard in most school systems; we use 'project-based' learning."
"For example," adds Walker, "The students are given a project to work on, such as Project Vote. In order to complete this project, the students must learn and utilize social studies, math, language arts and the technology. The educators are divided into teams that teach the subjects necessary for that project. There are only 20 students per class, but each student stays with the team until the project is complete."
"This style integrates teaching and learning at its best because the educators are not just a math, English, history or science teacher, but a combination-instructor of multiple subjects, which means all of our teachers are dual-certified," adds Fran Newberg, executive director for the office of educational technology. "It's an exciting adventure and I'm proud to be a part of it."
"We also have a person on-site to track all the technology and keep us current," says Chivis. "It's like a living, breathing plant. Everyday, we say, 'what's next'? And what's next is continually changing -- and that's always exciting."
The downside of technology
Some academic experts have said that too much reliance on technology can detract from teaching critical-thinking skills, and that students depend on computers too much, instead of thinking things through and doing the work themselves.
"Students are far too reliant on technology," says J. Andreas Lippert, associate professor of chemistry at Weber State University. "For example, I've noticed that they can't spell anymore because they always use the spell checker, which often results in incorrect word usage such as the difference between pulsar and pulser."
Lippert adds that students' reading capacity is also diminished because they scan everything so quickly; they don't retain anything they read. And worse, plagiarism is running rampant, because they copy and paste information directly off the Internet onto their papers, assuming that if it's on the Internet, it's free to use (as in public domain).
Additionally, the information retrieved from the Internet is often from less creditable sources, because the professionals and experts in their fields publish their research in books, which either cost money or require a trip to the library, continues Lippert. "I'm not against technology, because I certainly don't want to go back to the typewriter, but students today must learn to use the technology more wisely. Reading and writing are such critical skills; we can't allow them to become a lost art."
"New students are so familiar with technology in their personal life, they need these communication tools in their learning environment," adds Claire Schooley, an analyst at Forrester Research Inc. "We will not throw out the old-like classroom training. There will always be a place for that; but we must choose the appropriate format in order to learn faster and more efficiently. The new learners may not have the depth of knowledge ... but they will know how to find it easily when they need it."
"If there is a downside," says Westall, "it's the reality that this is an R&D school, which means there's a huge spotlight on it. We worry about letting outsiders see our failures when we're struggling to implement new products and processes. But we are growing accustomed to it. My only advice to other institutions planning similar projects is to just accept the attention (and the press) as part of the package. The trade-off is more than worth it!"
Sartain is a freelance writer in Utah. She can be reached at julesds@comcast.net.
IBM adds Linux apps support to Unix servers
 (IDG News Service) IBM has added a new feature to its virtualization platform that will allow Linux applications to run on IBM's Unix servers, the company announced Tuesday.
(IDG News Service) IBM has added a new feature to its virtualization platform that will allow Linux applications to run on IBM's Unix servers, the company announced Tuesday.The "Lx86" capability, to be included in IBM's PowerVM virtualization software, allows x86-based Linux applications to run on IBM's System p and Power-based Unix systems without modification, according to IBM. The systems will automatically detect and run Linux-based binaries designed for x86 environments.
"Lx86 is a way to say 'Whatever you have, it can run," said Scott Handy, vice president of marketing and strategy for IBM Power Systems.
The capability will simplify the consolidation of Unix and Linux server sprawls, Handy said. Running Linux applications in the Unix environment can reduce the cost of server consolidation and energy consumption and increase asset utilization, he argued.
Lx86 will be a useful tool for people looking to migrate from Linux systems to other IBM systems, IBM said. The company offers both Unix and Linux operating systems on its servers.
The capability will be included in all editions of IBM's PowerVM platform, which it also renamed Tuesday from the Advanced Power Virtualization platform.
The software now includes an Express edition targeted at small and midsize businesses. It allows customers to create up to three partitions on a server and control the use of processor cycles to get optimal performance. The Express edition will be shipped to customers soon, priced at $40 per core. PowerVM is also available in Standard and Enterprise editions.
IBM also announced that it will update its i5/OS operating system with support for Power6 processors. The update, called V6R1, includes improved performance, storage and security features, according to IBM.
The update supports IBM's Power6 EnergyScale technology for controlling energy use. The company also updated its Rational software tool set for the i5/OS, Handy said.
The i5/OS V6R1, for IBM's System i servers, will ship in March. It will also work with the company's new BladeCenter H server chassis, Handy said.
Microsoft adds new security APIs to Vista, XP
The new APIs will be included with Vista Service Pack 1, Windows XP Service Pack 3 and the brand-new Windows 2008 when those operating systems ship this quarter and next, said Michael Howard, a principal security program manager in Microsoft's security engineering and communications group.
According to Howard -- one of Microsoft's resident security gurus, who is probably best known for co-authoring Writing Secure Code -- the new APIs will allow more developers, particularly those still using older versions of ATL (Active Template Library), to call DEP in their apps.
DEP, which also goes by NX -- for No eXecute -- was introduced by Microsoft in Windows XP SP2 and expanded in Vista and Server 2008. It's designed to stop some kinds of exploits -- buffer overflow attacks, primarily -- by blocking code from executing in memory that's supposed to contain only data.
The new APIs can be used by developers working with the older ATL to enable DEP at runtime, or when the application actually launches. Previously, those programmers were forced to decide ahead of time whether their software would try to protect itself using DEP.
The most important of the new APIs is "SetProcessDEPPolicy," which sets the DEP policy for the running process, Howard said.
"When you link with the NX, it's cast in stone," explained Howard, referring to the use of ATL without the new APIs. "If you load a .dll that can't run correctly with DEP, it's not gonna work. With the new APIs, the cool thing is that you can have it in the configuration, so DEP is enabled by default -- so all the .dll [files] are protected." Those new APIs let the program opt in to DEP support when they're run, giving both developers and users more flexibility. Apps that rely on .dlls that won't work with DEP, perhaps because they're custom-created for the corporation and -- right or wrong -- use data areas of memory to execute code, can in turn opt out of the anti-exploit protection.
"We can now allow the application to be protected, even if the developer is using an old version of ATL," said Howard. "DEP is a good defense, and we want to make it easier for developers to use it."
The new APIs will also let programmers give control over DEP to users, he added. "If you support DEP but want to allow customers to disable DEP if there are serious compatibility issues, then this is the API to use because the argument can be a configuration option," he wrote in a technical post to his own blog on Tuesday.
The timing of the new APIs' introduction isn't a mystery, Howard said when asked why they are being rolled out now. "We're adding them to the service packs because they have such a high uptake" by users, he explained.
"We were much more aggressive in which components were protected [by DEP] in Vista compared to XP," said Howard. "And over time we will get even more aggressive. This is part of that."
Microsoft has slated Vista SP1 for release this quarter, though speculation has mounted that it will appear within a matter of weeks. Windows XP SP3 is scheduled to ship sometime in the first half of the year, while Windows Server 2008 has been tagged with a late-February launch date.
Computer ! My Love Today.

Knowledge Centers
Come to Computerworld Knowledge Centers to keep up with all the latest news, analysis and opinions on key enterprise technologies and issues. An index of main Knowledge Centers with their current top news stories is below:
Knowledge Centers
Operating Systems
Windows
Linux & Unix
Macintosh OS
Networking & Internet
LAN/WAN
Hardware & Devices
Protocols & Standards
Wireless Networking
Network Security
VPN
VoIP
Internet
Internet Business
Internet Applications
Web 2.0
SaaS
Broadband
Mobile & Wireless
Mobile Devices
Laptops
Mobile Access
Mobile Applications & RFID
Wireless Networking
Wireless Trends & Technologies
Personal Technology
Security
Cybercrime & Hacking
Spam, Malware & Vulnerabilities
Security Hardware & Software
Standards & Legal Issues
Privacy
Intellectual Property & DRM
Disaster Recovery
Storage
SAN
NAS
Hardware
Software
Disaster Recovery
Compliance
Storage Security
Business Intelligence
Analytics
Data Mining
Data Warehousing
Databases
Servers & Data Center
Servers
NOSes & Server Software
Data Center
Infrastructure Management
Grid & Utility Computing
Mainframes & Supercomputers
Disaster Recovery
Hardware
Processors
Windows & Linux PCs
Macintoshes
Laptops
Servers
Grid & Utility Computing
Mainframes & Supercomputers
Software
Desktop Applications
Enterprise Applications
CRM
ERP/Supply Chain
Open Source
Saas
Databases
Development
SOA & Web Services
Web Site Management
Software Development
Careers
Education/Training
Hiring/Recruiting
Skills
Search Job Listings
Outsourcing
Management
ROI
Project Management
Outsourcing
Government